It’s Important Because It’s Everywhere
Wi-Fi is an interesting topic because it’s everywhere and it’s become vitally important for most people in their daily lives, but often there are some security or quality concerns many users don’t consider. The following is the first in a series of blogs focused on Wi-Fi, and will cover home and office Wi-Fi tips to help improve security and privacy on small, locally managed networks. There are dozens of affordable and open source tools available that enable relatively low-skilled “hackers” to attack, jam, or collect data from Small Office Home Office (SOHO) Wi-Fi routers. These are just a few tips that can help your network from being the “low-hanging fruit” these script-kiddies often target.

How to Improve Wi-Fi Security and Privacy
- Update firmware – When installing a new wireless router, it’s generally a good idea to check for updates to the firmware. These updates are released to address security and performance issues for older builds, so skipping an update could leave you vulnerable to identified attacks, or your SOHO router could be missing out on the newest features that were released since it was purchased.
- Change the default settings – Out of the box, your new router will probably just work. Manufactures want to ensure consumers can easily plug it in and start streaming cat videos immediately. The initial router configurations are often set for convenience and not necessarily security, so it is recommended to take a moment to change some default settings. Here’s a short list of minor changes to improve your Wi-Fi security posture:
- Add a complex administrative password – default passwords are common knowledge and can be found all over the Internet. Take a moment to secure your router so visitors on your Wi-Fi network cannot access your management dashboard.
- Upgrade to HTTPS – Home Wi-Fi routers are often managed through a built-in web server where Users can make configuration changes. Often, these web servers are set to HTTP but can be upgraded to use HTTPS, providing additional protection against sniffing or collection attacks while accessing the management dashboard.
- Consider changing your default Service Set Identification (SSID) – The SSID is basically the name of your Wi-Fi network. Your SSID should be somewhat unique, to help prevent popular Rainbow Table attacks, while at the same time it should avoid grabbing unnecessary attention ( e.g. “FBI Surveillance Van”). Find a happy medium that your family and visitors can identify and remember.
- Don’t hide! – Many Wi-Fi routers allow you to hide, cloak, or disable broadcasting your SSID. This does little to add security to you network while it could pique the interest of script-kiddies eager to discover your hidden SSID.
- For each Service Set Identification (SSID) or network, add a complex passphrase and change it often – At home, we use an SSID for the smart devices (TVs, Roomba, etc.) that has an impossibly long and complex passphrae that I seldom change. For our daily devices (laptops, tablets, etc.), we use a separate SSID with a more user-friendly passphrase that I update more often.
- Disable Wi-Fi Protected Set-up (WPS) – WPS was intended as a literal easy-button for connecting and authenticating to a wireless network. Unfortunately, WPS had a disastrous roll-out due to short key implementation and while it was fixed, still leaves an unnecessary attack vector open. It is just easier to disable and ignore.
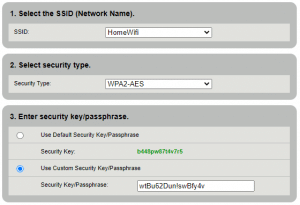
- Change your network’s security to Wi-Fi Protected Access (WPA) 2 or WPA3, if available. There are known attacks against WPA2 (which is why that complex passphrase is so important), but if WPA3 is unavailable, WPA2 is the next best thing.
- Vendors provide different options and names for Wi-Fi security and encryption. Unless you’re using some type of Enterprise authentication solution (e.g. RADIUS), you’ll want the option for “Personal” WPA2/3.
- Also, if there’s an option to choose a cipher suite, select GCMP for WPA3 or AES for WPA2.
- Enable Management Frame Protection (IEEE 802.11w) – While not always available, this option defends against outside attackers injecting malicious data into the network(e.g. deauthentication or replay attacks).
- Create a guest network/SSID – Most modern vendors offer a guest network option that prevents visitors from interacting directly with other devices on the network and from attempting to connect to the administrative dashboard. Users can still browse the Internet within this walled garden but they’re restricted from doing much else.
- Consider lowering transmit or output power – It is nice to get Wi-Fi in the farthest corner of your house, but how much further outside the walls is that signal penetrating? Unmanaged, a Wi-Fi signal can continue clear onto the next apartment or house, which means your streaming videos and Internet searches are being shouted into the ether for anyone to hear and potentially sniff or collect. Granted, the actual data is encrypted (since you hopefully set up WPA2 or WPA3) but why add the risk? Most businesses do not leave unattended Ethernet cables lying around their parking lots, and front lawns…think of Wi-Fi as the same thing and keep it indoors.
- Consider router placement – Similar to output power, is the router ideally placed to reach within your home where you need? If not located centrally, is it penetrating the walls deep enough that your neighbors can see your networks? Maybe directional antennas could keep the signal from bleeding outside, or a meshed network of smaller routers and access points would provide manageable coverage that serves the whole home with Wi-Fi without much bleed over.
- Set timing restrictions – Some SOHO routers include settings that will disable access during specific time periods. This is useful for disabling WiFi access to small offices during non-office hours and weekends.

This is just a short list of best practices for securing Wi-Fi at home and at work. In the future, we’ll discuss multi-band operations, mode and bandwidth selection, and other SOHO router configurations to help improve Quality of Service for small networks.