24 Feb11:28
24 Feb11:28
Feb 2023
Feb 2023
19 Jan12:03
19 Jan12:03
Jan 2023
Jan 2023
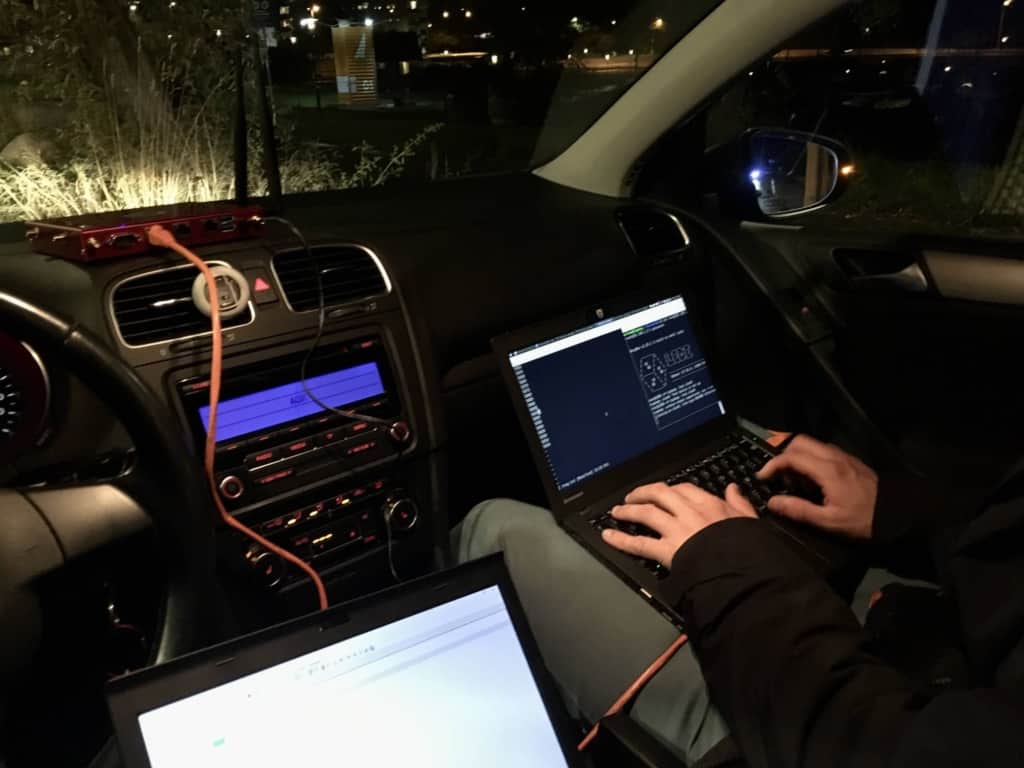
I'll show you how to set up a non-persistent secure mobile environment in just a few minutes....
06 Sep12:10
06 Sep12:10
Sep 2022
Sep 2022
The rapidly rising popularity of cryptocurrencies puts investors directly in the sights of criminals looking to steal more crypto for themselves....
14 Jul10:16
14 Jul10:16
Jul 2022
Jul 2022
Wigle.net contains almost 14 Billion records of Wi-Fi devices and their associated locations. We'll review how it’s used, how to avoid ending up in that list, and how to opt out if it’s too late...
01 Jul10:44
01 Jul10:44
Forming good habits will help keep you safe online and mitigate risks to your devices…
15 Jun10:42
15 Jun10:42
Jun 2022
Jun 2022
It’s important to know these essential terms because cyber security affects everyone….
01 Jun12:39
01 Jun12:39
Learn how to protect your information and devices from prying eyes while connecting to WiFi during travel....
16 May12:11
16 May12:11
May 2022
May 2022
While privacy on Android may seem impossible, there are steps you can take to improve it....
02 May12:02
02 May12:02
7-zip grants you an extra layer of security to protect important files....
15 Apr10:19
15 Apr10:19
Apr 2022
Apr 2022
Your phones care very little about your security and privacy out of the box….
01 Apr11:21
01 Apr11:21
Fortunately, Cryptomator makes it easy to quickly and securely encrypt data so users can have peace of mind that these cloud services cannot view or monetize their personal information....
28 Jan11:37
28 Jan11:37
Jan 2022
Jan 2022
The often-overlooked element of security is the insider who is already behind your wall of defense....
16 Dec12:00
16 Dec12:00
Dec 2021
Dec 2021
The vulnerability can easily be exploited to take control of affected systems remotely and allow hackers to practically do anything they want...
18 Nov12:28
18 Nov12:28
Nov 2021
Nov 2021
Since your webcam is likely in an area that you spend a lot of time, hackers can gain a great deal of information about you....
07 Oct11:27
07 Oct11:27
Oct 2021
Oct 2021
The rise of these bot services is alarming because it shows a flaw in how services use MFA....
26 Aug12:26
26 Aug12:26
Aug 2021
Aug 2021
While there are some fun uses for deepfakes, there are also many sinister ways they can be used to manipulate people...
22 Jul15:48
22 Jul15:48
Jul 2021
Jul 2021
Unlike with cryptography, steganography messages are readable to anyone with the tools to find them....
08 Jul15:07
08 Jul15:07
End-to-end encryption prevents outsiders from reading messages sent between a sender and receiver, whether it's email, text messages, voice, video, or any other form of modern communication.....
10 Jun15:05
10 Jun15:05
Jun 2021
Jun 2021
The bad news is you are increasingly likely to be the victim of a different kind of hostage situation....
01 Apr15:03
01 Apr15:03
Apr 2021
Apr 2021
Last week, Apple released a security update to address a zero-day, or previously unknown, vulnerability affecting IOS, IPadOS, and watchOS....
11 Mar16:12
11 Mar16:12
Mar 2021
Mar 2021
If not secured, an intruder could use the BIOS to initiate damaging attacks that could compromise your privacy, data, and system functionality....
11 Feb16:36
11 Feb16:36
Feb 2021
Feb 2021
Occasionally, I find something outrageous, like a scientific calculator app that requests access to my contacts. Just unnecessary....
21 Jan16:38
21 Jan16:38
Jan 2021
Jan 2021
Should you be trusting of any random QR code that you find? I don’t think so....
07 Jan16:31
07 Jan16:31
It may seem harmless for a hacker to steal control of your refrigerator, but there are ways it can be valuable to them.....