Wigle? Why not?
In the early aughts, when Wi-Fi really began taking off commercially and residentially, a new class of cyber tinkerers, hackers, and criminals created techniques of identifying and locating Wi-Fi routers to access the Internet for free– they coined this activity “Wardriving”. Back then, Wi-Fi security was fairly weak so finding a network often meant a Wardriver could also connect to and use that network. Wardriving has matured from laptops, GPS receivers, and a rats nest of cabling and antennas, into a simple application download for a laptop or smartphone. Also, the intent is no longer simply free Internet, but supporting and discovering useful information about particular network details and locations.
One such app is Wigle, or the “Wireless Geographic Logging Engine” which can record the locational information for thousands of nearby Wi-Fi devices before uploading the geo-referenced details to a public, crowd-sourced database for others to explore.
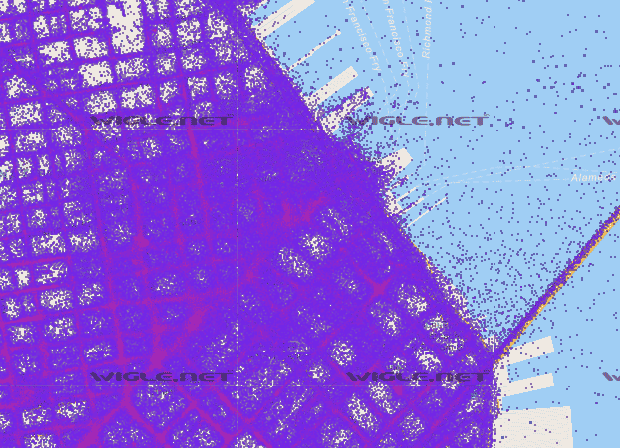
Each purple dot is a Wi-Fi device that’s been geolocated in San Francisco, CA
This open-source repository is a popular tool for Open Source Intelligence (OSINT) investigators and can be used to help refine the location of known network names or serial numbers. For example, if you’re searching for a Wi-Fi network with the name or SSID of “Muppet Pants”, a quick search in Wigle will provide the exact locations where a Wardriver’s Wigle app heard that network name. In this case, “Muppet Pants” was heard two times in Okinawa, Japan.
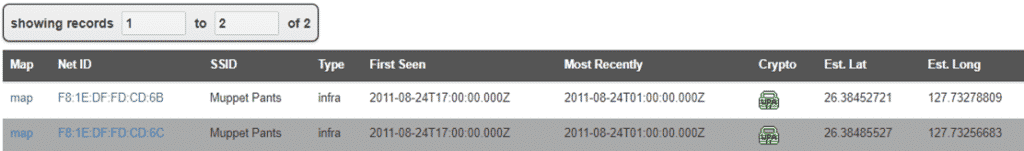
“Muppet Pants” search results in Wigle
By copying the Lat/Long details and pasting them into a Google maps search, you can learn more details about the nearby addresses or even have access to a street view of where that Wardriver was when they encountered “Muppet Pants”.
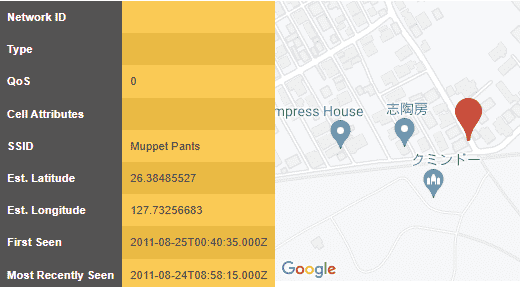
“Muppet Pants” map and details view

“Hey, that’s my house!”
To mitigate this type of research against your personal or business router information, there are a few steps you can take:
- Forget trusted/known networks
- When you join a Wi-Fi network with a smart device, it will often ask if the user wants to save or trust this network for the future. This allows the smart device to automatically join that network again in the future without re-entering a passphrase or choosing to “join this network”.
- A smart device will periodically transmit any trusted or known networks, attempting to locate and join those networks. This means a simple Wi-Fi sniffer nearby could hear all of the trusted or known networks associated with a particular user or device.
- Previously associated network names can help bad actors identify someone or their home’s location using tools like Wigle.
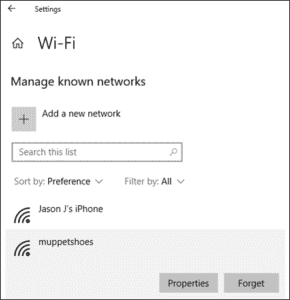
Example of forgetting known networks in Windows 10
- Disable Wi-Fi radio on your tablets, phones, and computers when not using them
- If a device’s Wi-Fi radios are turned off, that device won’t attempt to find its trusted or known networks.
- A nearby Wi-Fi sniffer won’t hear anything if the device’s Wi-Fi is turned off.
- When choosing a network name, find a happy medium
- You don’t want to be globally unique (like “Muppet Pants”), and you shouldn’t choose an old fashioned SSID like “Linksys” (which leaves you susceptible to rainbow table attacks which attempt to crack or discover your router’s passphrase). A good example of that happy medium is “Password is taco” which has 1,598 hits worldwide.
Finally, if you do find your network has been “Wardriven” and shared on Wigle, you can request that your information is removed from the database by emailing the Wigle site administrators found on the bottom of each page.
Was your home or office Wi-Fi seen on Wigle?
















