The Digital Wild West
 While surfing the vast waters of the internet, there is always a risk of predators lurking where you least expect them. Like sharks in the real world, viruses can wreak havoc on your computer if you’re not careful. It’s scarier than you might think because viruses are actually just one category of a larger family of malicious software known as malware. The simple definition of malware is any malicious program or code that is designed to damage, disrupt, invade, or steal data from computers, networks, or mobile devices.
While surfing the vast waters of the internet, there is always a risk of predators lurking where you least expect them. Like sharks in the real world, viruses can wreak havoc on your computer if you’re not careful. It’s scarier than you might think because viruses are actually just one category of a larger family of malicious software known as malware. The simple definition of malware is any malicious program or code that is designed to damage, disrupt, invade, or steal data from computers, networks, or mobile devices.
There are many different types of malware looking to infect your devices such as viruses, worms, trojans, and more that we will get into later in the blog. All of this sounds scary but don’t worry, the good guys (security researchers) are actively working to thwart malware before it can infect your devices, but the bad guys (malicious actors) aren’t going down easy. Even though the good guys are finding ways to detect and prevent malware from taking hold in your system, the bad guys are coming up with new ways to evade detection and making new malware that hasn’t been seen before. This is why your antivirus software needs updates so frequently and why it’s important that you do your due diligence to learn how to avoid malware infections.
The simple definition of malware is any malicious program or code that is designed to damage, disrupt, invade, or steal data from computers, networks, or mobile devices.
The Many Faces Of Malware
 When it comes to malware, there’s more variety than your local ice cream shop, except every flavor is bad. While the end goal of most malware is to damage your system or steal data from you, each type uses different methods to accomplish it. Once they get a foothold in your system they can hide in many different places while waiting to execute their attack. Let’s take a look at some of the different types of malware that you should look out for.
When it comes to malware, there’s more variety than your local ice cream shop, except every flavor is bad. While the end goal of most malware is to damage your system or steal data from you, each type uses different methods to accomplish it. Once they get a foothold in your system they can hide in many different places while waiting to execute their attack. Let’s take a look at some of the different types of malware that you should look out for.
- Virus – The most well-known type of malware. This is malicious code inserted into a program or application that looks to replicate and spread throughout the system once it is executed. An important note about viruses is that they require the user to execute the infected program before it can start to spread. Once the infected program is executed, the virus can begin to steal data, take control of applications, delete files, or send infected files to your email contacts.
- Worms – Very similar to viruses, a worm is also looking to replicate itself and spread across a system or network to cause damage. The primary difference between the two is that worms can replicate without any user action. This means worms spread much faster than viruses, making them much more dangerous.
- Ransomware – Ransomware is a type of malware that uses encryption to prevent the user from accessing their device or data. Once successful, the attacker demands a ransom to restore access to the user. The ransoms are usually very costly to pay and even if the user pays there is no guarantee that the device or data will be restored to normal.
- Trojan – This type of malware is disguised as a legitimate application and can usually perform the desired tasks. Behind the scenes it is also performing its malicious job of performing some harmful action on the computer or network. Trojans are commonly used to provide an attacker with remote access to the user’s system or network, where they can manipulate the system from any location.
- Spyware – Spyware is a type of malware that covertly gathers information about the user without their knowledge and sends it back to the attacker. The attacker is looking to breach your privacy and steal sensitive data from you such as your passwords. A popular form of spyware is a keylogger, whose primary function is to capture the keystrokes on the user’s keyboard but it can do other things like take screenshots.
Malware Sneaks Onto Your Device
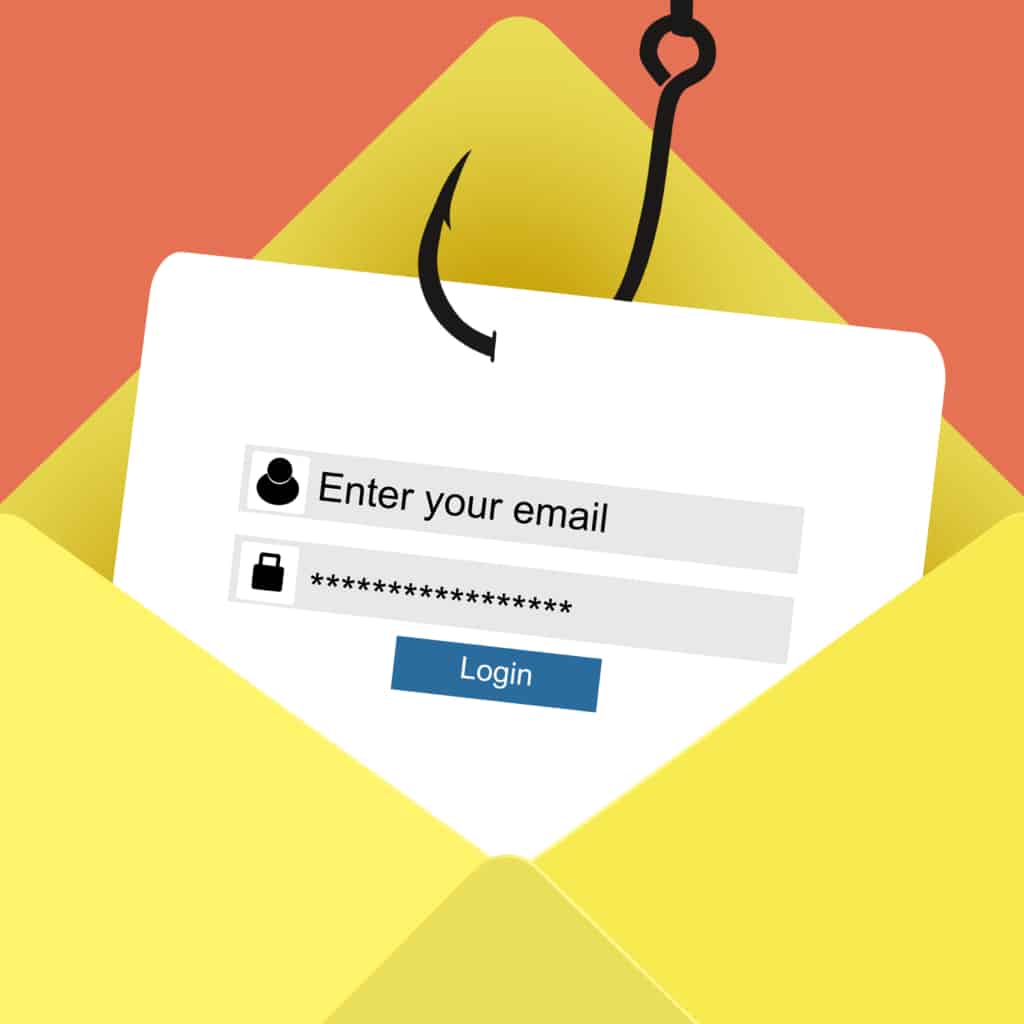
You might be asking why malicious people (attackers) create and spread malware to other people. Unsurprisingly their motivations aren’t much different than what motivates people to do bad things in the real world. Money, revenge, espionage, and sabotage are all reasons why someone would want to infect others with malware. Now that you know why they do it, let’s talk about how they do it. There are a bunch of ways malware can sneak onto your computer, but here are some of the most common methods:
- Downloads – Malware is commonly disguised as some desirable file or software that you are encouraged to download. It could be in the form of an email attachment, download link on a webpage, or a file on a file sharing service.
- Infected Websites – Attackers might send you a link to a website through email, social media, or messaging apps that have been compromised or deliberately designed to spread malware. Simply visiting the website is enough to trigger a malware download, without any indication to the user that this has occurred.
- Software Vulnerabilities – These are flaws in the software code that an attacker can exploit. When attackers discover these vulnerabilities they can use them to infect a device or network with malware.
- Infected external media – USB flash drives, external hard drives, CDs and other removable media can carry malware that will infect your computer as soon as you insert them. The attackers usually look for a way to either covertly insert the external media or they might try to trick you into doing it for them. Sometimes they might leave a USB flash drive on the ground in a high traffic area hoping that some unlucky person takes it home thinking they have just been gifted a free flash drive. Instead, they find a much more sinister surprise when they insert a flash drive and infect their computer.
- Social Engineering – A scammer attempts to trick users into downloading a seemingly harmless file that actually infects your device the moment you click it. Generally, their tactics include a combination of the first two methods discussed in this list. The scammer sends the downloads and links under the guise of an actual reputable entity, and it can be hard to spot the fakes. You can learn more about social engineering attacks in our previous blog here.
While the end goal of most malware is to damage your system or steal data from you, each type uses different methods to accomplish it.
Avoiding Digital Infection
 Malware can be scary, but the good news is there are many simple ways to protect yourself and your devices from being infected:
Malware can be scary, but the good news is there are many simple ways to protect yourself and your devices from being infected:
- Use antivirus software – a good antivirus software will help detect and block malware before it can infect your device.
- Update your software and system – Regularly updating your software and operating system will ensure that they have the latest security fixes to prevent them from being exploited by malware. Keep in mind that this includes updating your antivirus software so it can stay up to date on the latest malware.
- Be careful of email attachments and links – Simply put, do not click on any links or attachments from unknown sources. If the email looks suspicious in any way, don’t click the link. It’s often better to go directly to webpages to do things like password resets or to login to check a message on an account. To help you verify whether a link is legitimate, on most browsers and email applications you can hover over the link and it will show you where it will take you.
- Use secure authentication – You want to make sure you are using strong passwords or passphrases. Additionally, you want to consider enabling two-factor authentication on your accounts and devices. We have a blog on this here if you want some extra tips
- Be careful of what you download – You should only download software and files from reputable sources, which is usually the developer themselves. Untrusted third-party websites can be a trap and they might try to entice you by offering software at a discount or for free. Don’t fall for it. You should also be cautious when file sharing with random people or friends over the internet. They could unknowingly send you an infected file.
- Secure your web browser – you should be using a secure web browser that ideally comes with a popup and ad blocker enabled. Malware can hide in ads and popups and infect your devices when you click the ads or links in the popup window. For more advice on securing your web browser, check out our blog here.
With over 100 years of combined experience, OTA Training Specialists offer unique offensive and defensive techniques in cybersecurity, secure communications, and SIGINT training. Our training division, which can be reached at [email protected], would love to tailor training specifically to meet your needs. Click the button below to contact us.
Let us know what topics you’d like us to cover. We’d love to hear your suggestions and feedback. Click the button below to take a 1 minute survey.