In a previous post, we looked at some of the more obvious tells that indicated an email was likely from a mass-produced phishing campaign. Misspelled words, poor grammar, and grainy graphics are major giveaways that most non-technical users should be able to identify before clicking on a suspicious link. In this post, we’ll go a little further with normal online research and more technical tools to learn more about the email’s origin and identify this as a malicious email.
Now, a little open source research.
Remember that NYC address?  A quick web search reveals that it has nothing to do with Kohl’s corporate office…which is actually located in Wisconsin. In NYC, there is the Kohls Design office which is located on Broadway, but the address listed in the email actually points to a commercial 12-story office building in Manhattan’s Flatiron district that leases office lofts. Easy enough, but what else can we learn?
A quick web search reveals that it has nothing to do with Kohl’s corporate office…which is actually located in Wisconsin. In NYC, there is the Kohls Design office which is located on Broadway, but the address listed in the email actually points to a commercial 12-story office building in Manhattan’s Flatiron district that leases office lofts. Easy enough, but what else can we learn?
Email Header Clues
In most email clients you can view email header info, and here we see another giveaway that this message is potentially nefarious because the metadata indicated it failed the DKIM authentication.
| DKIM: | ‘FAIL’ with domain clamav.****pop.com |
DomainKeys Identified Mail (DKIM) is an RFC that addresses how senders can digitally sign their outgoing emails to authenticate their messages as originating from their domain. It was designed to help “assist in the global control of ‘spam’ and ‘phishing’,” so failing this is a pretty significant flag.
Sleuthing Online
Using some online tools like network-tools.com and domaintools.com, we discovered that the subdomain clamav.****pop.com is hosted by Worldstream Latam B.v and operates on a dedicated server at IP address 190.***.133.41. I’m not familiar with Worldstream Latam, but they’re probably like many other hosting companies, like AWS, Digital Ocean, and WordPress. They simply offer their services to paying customers and aren’t aware of any nefarious behavior.
Something else that was interesting is that the parent domain, ****pop.com is hosted by the same organization at 190.***.133.39 so I tried some of the nearby IP addresses and found the following:
****pop.com – 190.***.133.39
hilton.****pop.com – 190.***.133.40
clamav.****pop.com – 190.***.133.41
olive.****pop.com – 190.***.133.42
The email originated with the clamav.****pop.com domain name, which was registered through Enom Inc (Kind of like GoDaddy), and the physical server locations for its IP address appears to be located in Holland.
Netcraft provided a risk rating of 9/10, which indicates that the site poses a significant risk, however Virustotal produced an automated report that cleared the site of hosting any sort of known malware…so hopefully we’re not walking into a ransomware attack.
The Whois records only point to the authoritative resource, Latin American and Caribbean Internet Address Registry (LANCNIC), which indicates the owner spent a little extra money to mask their personal details and instead point only to that single authoritative resource.
Wrap Up
We could get into more technical tools, and learn more about what Operating System the servers are running, what additional services, ports, and protocols are being used, but we’re sticking with mostly online not-so-technical tools for discovery.
Before we wrap this up I will share a quick screenshot of what happened when you clicked on the email that linked to clamav.****pop.com. I’ll note that the URL changed, and the site’s behavior changed dramatically, depending on if I was connected to a VPN, refreshed the page, or allowed the timer (pictured below) to expire.
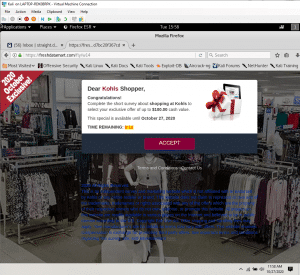 Check in next week as we dive in and click “accept” to see what happens. We’ll also review the obscenity-laced source code and see what else goes on during some of these phishing attacks.
Check in next week as we dive in and click “accept” to see what happens. We’ll also review the obscenity-laced source code and see what else goes on during some of these phishing attacks.