I noticed this morning that a series of emails with odd subjects lines were filling up one of my personal email inboxes. It’s not unusual, I’m probably a little too online for my own good. But I wanted to see what we could learn about phishing attacks starting with a cursory review of the email itself, just doing the basics to spot and avoid being tricked. Then we’ll go a little further by doing a little more technical research, and finally we’ll just let loose and click on all of the things within a safe environment.
First let’s look at some of the dead giveaways that this wasn’t a normal email.
My Initial Review
The email subject was “Attn: <email handle> Your 100$ Kohls Reward Has Arrived. 2HNZ”.
This triggered my Spidey Senses.
- The email used my email handle. If this was a department store I’d previously visited, they’d probably use the first name I provided when signing up for their email list
- 100$ doesn’t make any sense
- The capitalization throughout seemed awkward to me. I’m sure a chain department store would be more deliberate in their online marketing campaigns
- Finally, it included a strange message at the end, “2HZN”. I’m not sure what that’s about
Additionally, the email was sent by an alias called “Congrats!” with an email address of Service@clamav.****pop.com which does not ring a bell. I’m familiar with clamav, the fantastic open source antivirus tool, but not the domain “****pop.com”. Curious.
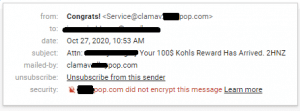
So, all that was viewable from just my email client without really clicking on anything.
Digging Deeper
DISCLAIMER!
I opened up the email to see what was inside but do not recommend you do this. It’s probably best to flag it as spam or phishing and move on. However, in the pursuit of knowledge, we drive on.
From the safety of a trusted sandboxed environment, OTA’s Catfish remote browser, I clicked on and opened the email. Inside, I found a small hyperlink that says “Hi” that sits on top of a grainy image of a $100 Kohl’s gift card. The hyperlink directs us to that domain clamav.****pop.com…not Kohls.

Hovering over the grainy gift card image, I can see that this email’s graphics are hosted by googleusercontent.com, which is a legitimate Google Content Delivery Network (CDN), however in the URL there is reference to the same ****pop.com domain. We really need to figure out what ****pop.com is.
Now, the gift card image includes some text with some more odd capitalization but there are some other interesting variations. For instance, the value of the card is identified correctly, as $100 and not 100$. Seems careless.
The lower portion of this graphic includes a “button” which is just part of the main image – that is, it’s not a button, just meant to look like a button. In fact, the entire image, seen above, is one giant button which links to the same clamav.****pop.com site from above.
Below the gift card image is a second smaller image, this one containing the “Unsubscribe” link and an address, presumably of the Kohl’s corporate office. This links to clamav.****pop.com as well.

On just the surface, we were able to learn that the “Hi” hyperlink, the “Gift card” image, and the “Unsubscribe” image/link all take you to the same destination at clamav.****pop.com, all media content is hosted through Google’s CDN, and there are pretty obvious capitalization issues and that variation with the gift card amount.
Telltale Signs Of A Phishing Email
Let’s review more telltale signs that an email is a likely phishing attack:
- Real businesses will probably address you by your name; phishers probably won’t
- Real businesses will email you from their domain; phishers cannot
- Real businesses are particular about grammar, spelling, and punctuation; phishers probably are not
- Real businesses are also particular about their graphics, branding, etc.; phishers probably are not
- Real businesses should send you to their legitimate website; phishers will try to send you to their website
- Real businesses shouldn’t trick you into visiting their website (e.g. creating the entire email content to be a hyperlink that opens a new tab or window); phishers may attempt this
- Real businesses won’t ask you personal information; phishing emails often do, or point you to a website that will ask for personal details
- Real businesses won’t include unsolicited attachments; phishers can and do this often
In this example Kohl’s gift card email, we’ve found 6/8 of the above telltale signs. Your Spidey Senses should be going off!
Join us next week as we dive a little deeper into more research techniques. We’ll find the hosting company, associated IP addresses, the domain name’s registrar, and any Whois records about the organization behind this phishing email.