BLUF
When powering on a computer, there’s a “ghost in the machine” that runs in the background, known as the BIOS. Before the operating system is loaded this transparent process is responsible for waking up your computer, identifying the hardware, and configuring settings. The BIOS is the first software that runs on your computer and you can access it to modify many security settings. Most users don’t realize just how much can be modified in the BIOS and that it should be protected with a strong Administrator Password. If not secured, an intruder could use the BIOS to initiate damaging attacks that could compromise your privacy, data, and system functionality.
The BIOS and Why it could be Targeted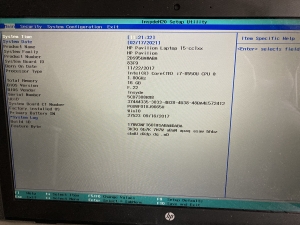
BIOS stands for Basic Input Output System and usually appears plain without much fanfare, and users are often restricted to keyboard input only. The BIOS is on its way out, as more vendors are moving toward the UEFI, or Unified Extensible Firmware Interface, which include more capabilities and administrative controls, and often features a more aesthetic or functional user interface (e.g., you can use your mouse!).
The legacy BIOS and the modern UEFI both behave like low-level software that first checks your system settings and then boots the Operating System, say, Windows 10. Most of this work is done behind the scenes and is transparent to the user unless they are alerted by an audible honk or screech that an error has occurred. The BIOS/UEFI contain various settings to change hardware configurations, reorder the boot sequence, and enable or disable advanced options.
It is easy to overlook the BIOS/UEFI because it runs in the background, but many of those settings can seriously impact a user’s privacy or the system’s functionality. Intruders could disable features like Secure Boot, which ensures that the computer must power-on with the same components as when it was powered-off. In a computer that isn’t protected by Full Disk Encryption, like Bitlocker, an intruder can mount something called a sideload attack and steal all the computer’s data, effectively going around your Operating System’s security controls, and accessing user data directly. An intruder could even go so far as to discover a BIOS/UEFI password has not been set, and set one themselves, effectively locking you out of your own computer’s settings. No good.
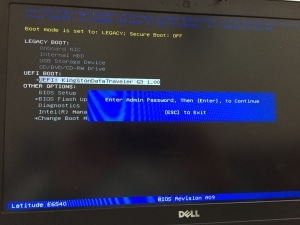
How to Protect the BIOS
The best way to prevent intruders from easily accessing the BIOS/UEFI is to enable a System or Administrator password authentication. To do so, you’ll need to access your computer’s BIOS/UEFI menu, which can usually be accomplished by pressing a hotkey like Esc, F2, or F10 (depending on the vendor or manufacturer) when powering on the device. Windows users have a few more options to get into their BIOS/UEFI menus:
- When at the login screen, click on Power, and hold the “Shift” key down while clicking on Restart.
- After successfully logging in to your account, press the “Windows” key to bring up the Start Menu, click the Power button, and hold the “Shift” key down while clicking Restart.
- After successfully logging in to your account, press the “Windows” key to bring up the Start Menu, and type “restart” which will bring up an option to “Change Advanced Startup Options”. Click that and select Restart Now under Advanced Startup.
Each of these three options will take you to the Advanced Startup menu. From there, click Troubleshoot, then Advanced Options, then UEFI Firmware Settings, and finally the Restart button. This should redirect you to your system’s BIOS/UEFI menu.
Once in the BIOS/UEFI menu, look around the security settings to find the possible password options. Unfortunately, the specific accounts/passwords and their purposes are unique to each vendor/manufacturer, so it may be called Administrator, or System account, but there is often a description beside each password setting to explain its details. Some of the options may require a password to access the BIOS/UEFI, or instead require the password to change any BIOS/UEFI settings. Some even prevent the computer from booting-up until the BIOS/UEFI password is entered successfully. After choosing a password option and setting a complex password, you should restart and check that everything is working correctly.
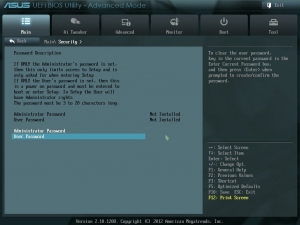 One last word about BIOS/UEFI passwords. Like anything else, a password is not a guarantee for total protection. A determined intruder could still reset your password security by opening your device and removing the CMOS battery, but that takes time and patience, especially with a laptop. Ultimately, we’re creating hurdles to deter unauthorized access to your computer’s sensitive settings and confidential data.
One last word about BIOS/UEFI passwords. Like anything else, a password is not a guarantee for total protection. A determined intruder could still reset your password security by opening your device and removing the CMOS battery, but that takes time and patience, especially with a laptop. Ultimately, we’re creating hurdles to deter unauthorized access to your computer’s sensitive settings and confidential data.